
Kerberos Flow
Security Requirements
Kerberos is the most secure Integrated Windows authentication protocol and supports advanced security features including Advanced Encryption Standard (AES) encryption and mutual authentication. The main advantage of Kerberos over NTLM or forms-based authentication is the ability for a user’s identity to securely traverse multiple servers without requiring a re-key of the user’s credentials. This concept is referred to as single sign-on: login once to access everything. A secondary advantage is speed. Authenticating connections with Kerberos tokens is considerably faster than other methods.
Kerberos Advantages
- Most secure
- Enables delegation
- Open protocol
- Least amount of network traffic
Kerberos Disadvantages
- Extra configuration steps are required on the Central Administration server and in the domain’s DNS, see the section Kerberos Implementation for details. NTLM can be implemented and later switched over to Kerberos. This would be advantageous if there are possible delays in the Kerberos prerequisites.
- Final URL’s must be determined before Kerberos can be implemented on the SharePoint site.
Kerberos Flow
The diagram below depicts a typical Kerberos flow.
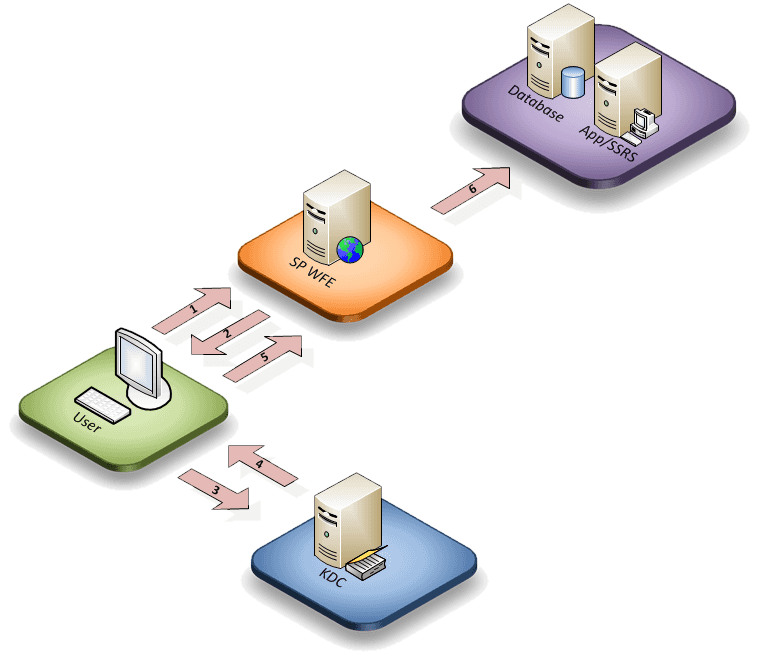
- User navigates to http://www.site.com without a ticket
- User is automatically redirected to KDC for a ticket.
- User authenticates with KDC/AD
- KDC issues a ticket for use on web application and automatically redirects user back to application
- User now has access to site
- Ticket is reused via delegation to access backend services without new communications with KDC or AD
Kerberos Implementation
This section describes the steps required to implement Kerberos on a SharePoint site. It assumes the steps will be implemented by someone with DNS, load balancing and SharePoint experience.
- For this example, the site will have an internal URL of portal.domain.com and the service account used in the SharePoint application pool for the IIS web will be corp\svc-sp2010-webpool-d
- Create a load balanced IP for the web front end servers
- Open DNS snap in
- Create a host (A) record for the load balanced IP address with the fully qualified domain name
- On the Central Administration server, create an SPN for corp\svc-sp2010-webpool-d for portal.domain.com by executing the following command:
setspn –s HTTP/portal.domain.com "corp\svc-sp2010-webpool-d" - Grant delegation privileges to the service account (needed only once per account)
- Open Active Directory Users and Computers snap in
- Open the properties window for corp\svc-sp2010-webpool-d
- Click the Delegation tab
- Select “Trust this computer for delegation to any service (Kerberos only)”
- Create the SharePoint application using a host header of portal.domain.com
- Testing Kerberos
- On a client machine, launch a command window
- Execute the following to clear existing Kerberos tickets:
klist purge- Browse to portal.domain.com
- Execute the following to view new Kerberos tickets:
klist- Validate that the cached tickets count is greater than 0
Converting to Kerberos
- Perform steps 1 – 6 in the section Kerberos Implementation
- Go to SharePoint Central Administration -> Manage Web Applications
- Select the desired web application
- In the ribbon, click Authentication Providers
- Click the zone
- Scroll down to Integrated Windows Authentication
- Change NTLM to Kerberos
- Click Save
- Do an IIS reset
- Test Kerberos by performing step 8 in the section Kerberos Implementation